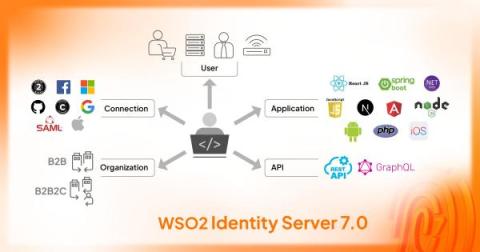
Mastering API Gateway Auth: Proven Methods for Secure Connectivity
Securing your API gateway is critical to protect your services from unauthorized access and ensure safe data transmission. In this article, we’ll explore the essentials of API gateway auth, discuss the major authentication methods, and offer guidance for implementing and overcoming challenges in API gateway authentication—providing you with the knowledge to keep your digital assets secure.