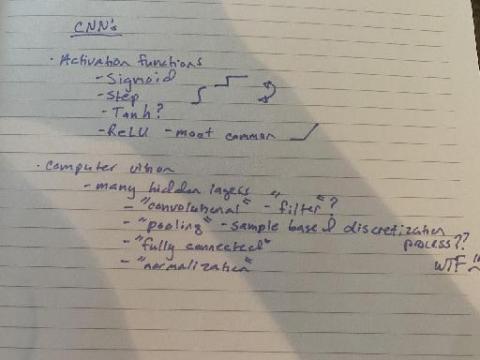
WTF is a Convolutional Neural Network?
If you are a software engineer, there's a good chance that deep learning will inevitably become part of your job in the future. Even if you're not building the models that directly use CNNs, you might have to collaborate with data scientists or help business partners better understand what is going on under the hood. In this article, Julie Kent dives into the world of convolutional neural networks and explains it all in a not-so-scary way.