Get Gravitas and Go Amazonian: Kong Validated for AWS Graviton3, Amazon Linux 2023 OS
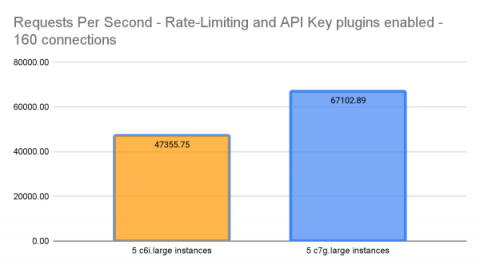
Today, we’re thrilled to announce that Kong Enterprise and Kong Konnect Data Planes are now validated to run on AWS Graviton3 processors and Amazon Linux 2023 OS. As an APN Advanced Tier Partner of AWS, we were delighted to have the opportunity to benchmark Kong Enterprise running on AL2023 and Graviton3.