Creating Effective Test Plans: A Guide to Success
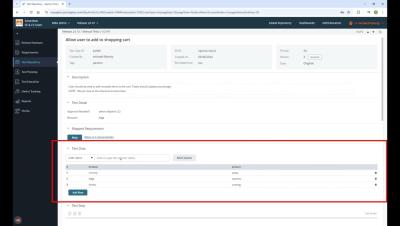
Imagine being at the helm of a project, excited to launch an innovative software application, but then... the testing phase reveals critical flaws that could have been caught earlier. This experience is a stark reminder of how vital a cohesive test plan can be. Join me as we explore how a visual test plan builder can transform your approach to crafting robust test plans, ensuring quality at every step of the way!