Systems | Development | Analytics | API | Testing
%term
How to Ignore Files and Directories in Perforce Helix Core
5 Generative AI Use Cases You Need to Apply to Your Processes
Ready to implement generative AI in your business processes? Starting with the right generative AI use cases is key to your success. You’ll want to find areas where you can achieve quick wins as you grow toward your larger AI vision. In this article, we’ll highlight five use cases where you can incorporate generative AI for increased process efficiency.
The 2023 Kong Year in Review
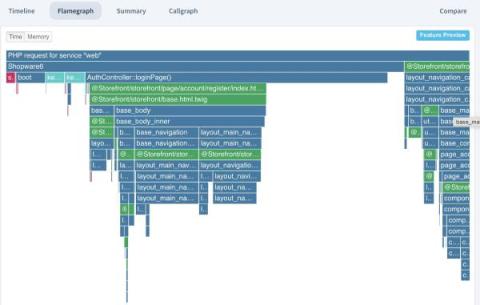
Flamegraph Feature Preview Christmas Present, Thank you for 2023!
As a Christmas present, we have started rolling out a new feature for the Profiler: flamegraph rendering in addition to the existing Timeline and Callgraph. This is a feature preview and will see more changes in Q1 of 2024. For now, only customers with the most recent plans (Tideways 6) can access them, or you can view them in traces of the „demo“ organization. Let us know what you think of it!
Layered Security Strategy for Managing APIs
What Is Automated Regression Testing, and How Do You Get Started?
10 Testing Recommendations for Software as Medical Device
Medical devices have been used for centuries but are only being regulated recently to ensure patient safety. Every medical device must meet the requirements of the regulations in a country or region before entering the market. Very recently, going digital has changed not only our lifestyles but also the operations of medical devices.