Systems | Development | Analytics | API | Testing
Blog
Kubernetes Ingress gRPC Example With a Dune Quote Service
APIs come in all different shapes and forms. In this tutorial, I’ll show you a Kubernetes Ingress gRPC example. I’ll explain how to deploy a gRPC service to Kubernetes and provide external access to the service using Kong’s Kubernetes Ingress Controller. And to hype you up a little bit about the upcoming live-action movie, Dune, based on Frank Herbert’s book, I created a Kubernetes service that delivers Dune quotes.
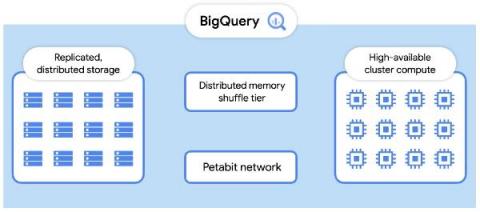
BigQuery Admin reference guide: Query processing
BigQuery is capable of some truly impressive feats, be it scanning billions of rows based on a regular expression, joining large tables, or completing complex ETL tasks with just a SQL query. One advantage of BigQuery (and SQL in general), is it’s declarative nature. Your SQL indicates your requirements, but the system is responsible for figuring out how to satisfy that request. However, this approach also has its flaws - namely the problem of understanding intent.
A Window of Opportunity to the Data Cloud
When Apple launched its App Store in 2008, it opened a window of opportunity for thousands of software developers who rushed to invent the mobile-first world in which we all live today. Vendors that embraced the new paradigm, such as game developer Imangi, saw breakthrough success.
Free Cycle Time Readout for GitLab Users
To celebrate GitLab’s latest release and GitLab Commit 2021 we offer free cycle time readout of all of your personal and company projects hosted on GitLab.com for a limited time. Use this link and your GitLab credentials to sign into Logilica Insights and we let you know about your software teams cycle time, delivery velocity and much more.
Securing Your SQL Server Application: Enabling Server-Initiated Encrypted Connections
Network encryption is a vital security step in hardening your application and guarding your data. Additionally, it is more often becoming a requirement by many organizations and laws (like HIPAA). In this article, we will discuss how to secure network communication between your application and the SQL Server database using an encrypted connection. We will demonstrate how encryption can be enabled and leveraged from SourcePro DB with no source code changes to your application.
The Dark Truth Behind Session Recording
A company is entitled to use session recording or session replaying as long as their marketing and analytics needs require so. However, as enticing the recording of everything the user does at all times can be, even within the existing regulations, there is a high chance that doing so will quickly push the data towards a non-compliant realm. And even in cases where regulations may not be explicit on the matter, we see more and more how the industry is leaning towards discouraging these practices.
The Top 21 Grafana Dashboards & Visualisations
In our guide on the best Grafana dashboards examples, we wanted to show you some of the best ways you can use Grafana for a variety of different use cases across your organisation. Whether you are a software architect or a lead DevOps engineer, Grafana is used to make analysis and data visualisation far easier to conduct for busy engineering and technical teams throughout the world.
Reflections on Leadership: A Fireside Chat with mentor(SHE:) and Yellowfin
The Real Cost of API Downtime
Last week, the digital world experienced a power outage. A major distributed edge computing platform experienced a software bug that led to the collapse of their Domain Name System (DNS), or the Internet’s way to map domain names (i.e. united.com) to IP addresses. The consequences were costly. So what is the real cost of downtime? When a DNS system within a globally recognized edge platform fails, it causes downtime for a huge amount of international enterprises.