Systems | Development | Analytics | API | Testing
%term
Run Selenium Java Tests on Different Browsers on Sauce Labs
Run Java Tests in Parallel on Sauce Labs
Rollbar Tip of the Day: Filter by Date Range
k6 v0.33.0 released
It's once again the end of a release cycle for us here at k6, and this time we're happy to announce that k6 v0.33.0 is here! 🎉 The v0.33.0 release is a small one, mainly containing a bunch of minor bugfixes and enhancements, but is also laying the groundwork for some major new features like the upcoming k6/execution API in k6 v0.34.0. To read the full release notes, see the GitHub Release for v0.33.0.
Configuring a Kubernetes Application on Kong Konnect
Hello, everyone! Viktor Gamov, a developer advocate with Kong here. In this article, I would like to show you how to set up service connectivity using Kong Konnect and Kubernetes. I will deploy an application in Kubernetes, configure a runtime through Konnect and demonstrate some management capabilities like enabling plugins. Let’s dive right in!
Fastlane actions that make a developer's life easier
Fastlane actions are built-in commands (actions) for which you don’t need to install any plugin or 3rd party tool. In this article, we will discuss the most commonly used fastlane actions that are useful for anyone who works in mobile development.
JWT Authentication: When and How To Use It
JWT stands for JSON Web Token, is a famous technology that comes with its own controversy. Few people find it quite beneficial, while others feel one must never use it. Nonetheless, in this article, we shall discuss the reason behind this controversy, understand JWT in detail, and when and why one must use it. We'll cover the following section in this blog. JWT (JSON Web Token) authentication is a process or method used to verify the owner of JSON data.
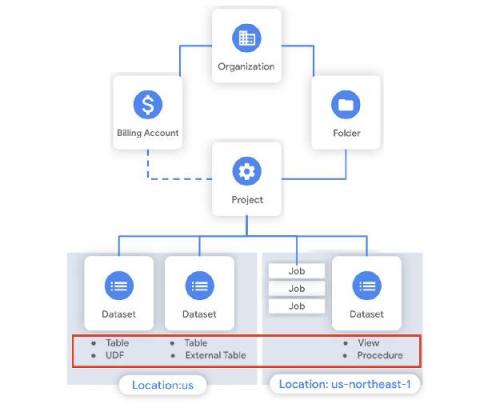
BigQuery admin reference guide: Tables & routines
Last week in our BigQuery Reference Guide series, we spoke about the BigQuery resource hierarchy - specifically digging into project and dataset structures. This week, we’re going one level deeper and talking through some of the resources within datasets. In this post, we’ll talk through the different types of tables available inside of BigQuery, and how to leverage routines for data transformation.
Interview With Cybersecurity Expert Tom Kirkham
For our latest expert interview on our blog, we’ve welcomed cybersecurity specialist Tom Kirkham to share his wealth of experience on the topic of cybersecurity. Tom is the founder and CEO of IronTech Security, a managed security service provider (MSSP) that focuses on educating and encouraging law firms, court systems, water utilities, and financial firms to establish a security-first environment with cybersecurity training programs for all workers to prevent successful attacks.