Systems | Development | Analytics | API | Testing
Security
Behavioral Authentication: Improving Security and CX Without Compromise #WordsUnplugged
Sauce Labs Upholds Security Commitment with ISO 27001 and ISO 27701 Recertifications
What Is API Gateway Authentication?
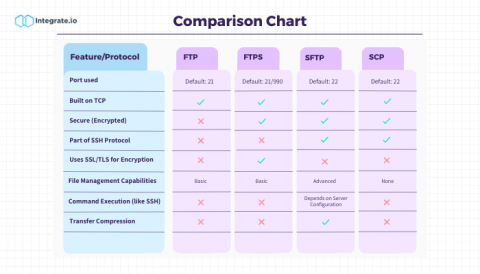
The Complete Guide to FTP, FTPS, SFTP, and SCP
In the digital age, data transfer is integral to operations for businesses of all sizes. While Extract, Transform, and Load (ETL) processes have become fundamental for moving raw data to destinations like data warehouses, the protocols you use to transfer these files can impact the efficiency and security of the entire operation. Dive into our comprehensive guide, as we shed light on the most popular file transfer protocols and their relevance in today's tech landscape.
How Secure is SFTP?
Securing CI/CD with 1Password
Secret management in shared environments like Continuous Integration and Delivery services is challenging. It’s essential to keep secrets secure and ensure they don’t end up in the wrong place, like logs or code repositories. Integrating solutions like 1Password into CI/CD workflows offer the advantage of centralising secret management, and it also allows you to encrypt every secret, providing controlled programmatic access to applications.
Reduce API Security Risks with Standardized Governance
APIs serve as the foundation for how software systems and services communicate and exchange data. But unmanaged and unsecured APIs can open up massive vulnerabilities that lead to disastrous security breaches and data leaks without proper governance. With API-related attacks increasing — and set to increase 996% by 2030 — unmanaged APIs are a very real security threat. How do you implement reliable API security without slowing down innovation or blowing up costs?
How to Ensure Supply Chain Security for AI Applications
Machine Learning (ML) is at the heart of the boom in AI Applications, revolutionizing various domains. From powering intelligent Large Language Model (LLM) based chatbots like ChatGPT and Bard, to enabling text-to-AI image generators like Stable Diffusion, ML continues to drive innovation. Its transformative impact advances multiple fields from genetics to medicine to finance. Without exaggeration, ML has the potential to profoundly change lives, if it hasn’t already.
Enhance Your Cyber Defense with Red Teams as a Service: Strengthening Security Strategies
According to the most recent statistics, on a global scale, approximately 1 in 31 organizations encountered a ransomware attack each week during the initial quarter of 2023. Additionally, there is a daily identification of over 560,000 new instances of malware, contributing to a staggering total of more than 1 billion malware programs currently in circulation.