Systems | Development | Analytics | API | Testing
%term
How to Properly Leverage Elasticsearch and User Behavior Analytics for API Security
Kibana and the rest of the ELK stack (Elasticsearch, Kibana, Logstash) is great for parsing and visualizing API logs for a variety of use cases. As an open-source project, it’s free to get started (you need to still factor in any compute and storage cost which is not cheap for analytics).
What is Serverless Computing?
How to Move from Basic to Advanced Marketing Analytics in Four Steps
Advanced marketing analytics can improve campaign relevance, increase customer lifetime value, accelerate insights, reduce acquisition costs, and drive ROI. But moving to advanced analytics requires a thoughtful investment in the right infrastructure for storing, tracking, and analyzing customer data, which can be daunting to companies that only have basic analytics capabilities.
Announcing the Fivetran dbt Package for HubSpot
Use our dbt package for HubSpot to build your sales and marketing dashboards.
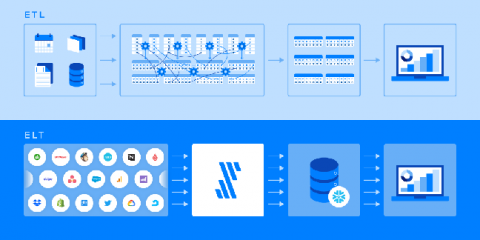
A Beginner's Guide to ELT Data Pipelines
Learn why ELT is better than ETL and how you can get started with it.
How TelemetryTV Used Databox to Cut Reporting Time, Reduce Meetings, & Make Improvements Faster
How To Accelerate API Integration with Behavioral Emails and Developer Segmentation
Behavioral email is the keystone of user-centric platform integration — emails to developers are most effective when they’re based on how they used your platform. Not surprisingly, the concept of segmenting your customers into groups of similar behaviors or attitudes is a well established best practice in marketing. MarketSherpa’s survey found that one of the most effective marketing strategies is to send emails based on the behavior of your customers.
The State of Elixir HTTP Clients
In today’s post, we’ll look at two Elixir HTTP client libraries: Mint and Finch. Finch is built on top of Mint. We’ll see the benefits offered by this abstraction layer. We’ll also talk about some of the existing HTTP client libraries in the ecosystem and discuss some of the things that make Mint and Finch different. Finally, we’ll put together a quick project that makes use of Finch to put all of our learning into action. Let’s jump right in!
Protecting Your Apps From Link-based Vulnerabilities: Reverse Tabnabbing, Broken-Link Hijacking, and Open Redirects
Links are so fundamental to web development that they're almost invisible. When we link to a third-party page, we hardly ever consider how it could become an opportunity to exploit our users. In this article, Julien Cretel introduces us to three techniques that bad actors can use to target our users and discusses how to avoid them.