Systems | Development | Analytics | API | Testing
Latest Posts
Data Wrangling vs. ETL: What's the Difference?
14 Top API Management Tools for 2024
How Change Data Capture Cuts Costs and Modernises Applications in a Competitive Market
Unlocking the power of semi-structured data with the JSON Type in BigQuery
Explore the architectural concepts that power BigQuery’s support for semi-structured JSON, which eliminates the need for complex preprocessing and provides schema flexibility, intuitive querying and the scalability benefits, at large scale.
How to authenticate a Next.js Route Handler using Clerk
When building web applications you’ll often be using services on the client that require authentication. A common way client-side SDKs like Ably authenticate themselves is by using server-side API endpoints that generate and return access tokens. Using access tokens allows you to keep your service’s secrets on the server and instead issue time-limited and scope-limited tokens to a client. Some services even let you create revocable tokens for added security.
How to Handle CSV Files Over SFTP: Best Practices
insightsoftware Named No. 1 Fastest Growing Company on Business North Carolina's Mid-Market Fast 40 List
Scaling MLOps Infrastructure: Components and Considerations for Growth
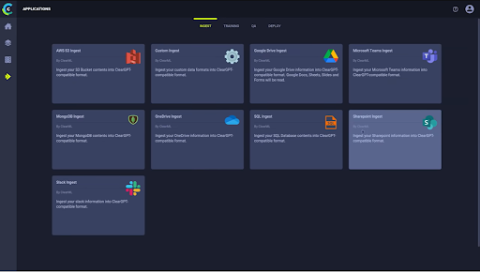
How to Build Accurate and Scalable LLMs with ClearGPT
Large Language Models (LLMs) have now evolved to include capabilities that simplify and/or augment a wide range of jobs. As enterprises consider wide-scale adoption of LLMs for use cases across their workforce or within applications, it’s important to note that while foundation models provide logic and the ability to understand commands, they lack the core knowledge of the business. That’s where fine-tuning becomes a critical step.