Systems | Development | Analytics | API | Testing
Kong
Kong Mesh Quickstart for OpenShift 4.12
Streamline Service Mesh Observability with Kuma & OpenTelemetry
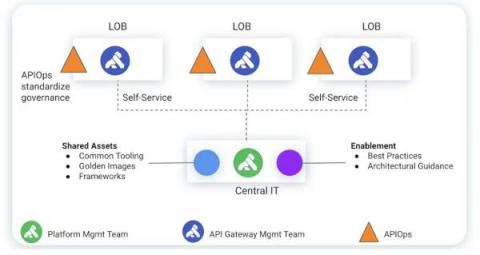
API Platform and Data Mesh: Why Bring Them Together
Enterprises are investing in data mesh initiatives to accelerate how decisions are made and to create novel experiences based on machine learning models. Similarly, enterprises are investing in API platform initiatives to productize business domains (or bounded contexts in domain-driven design parlance) as self-service digital assets that accelerate innovation and improve business agility. Both initiatives are typically run as separate work streams.
What's New in Kong Ingress Controller 2.10?
We’ve just shipped Kong Ingress Controller (KIC) 2.10! This release makes KIC easier to use. In this blog we’ll cover: You can read the CHANGELOG for full details, but for now, let’s focus on the highlights.
In the Driver's Seat with Konnect - Uplevel Your API Management Strategy
Guide to API Testing: Understanding the Basics
APIs come in many different shapes and sizes and have been around for a long time. Whether you are brand new to the topic or think about your day-to-day in terms of RESTful methods, you are using APIs every day. “This morning I PUT on my clothes, went to the kitchen to GET a cup of coffee, sat at my computer and felt the satisfaction of finding emails to DELETE that don’t need any action from me. My morning ended up being pretty 200 OK.”
Zero Trust Security: The What, Why and How
If you’ve been researching API security, you’ve likely seen the term “Zero Trust.” And you may already know that organizations can use Zero Trust to help protect their APIs from attacks. What you may not know is that Zero Trust is one of the best models for API security. According to Microsoft, “96 percent of security decision-makers state that Zero Trust is critical to their organization’s success.” But what is Zero Trust exactly?
Understand the Differences: API Authentication vs API Authorization
If you landed on this blog post, chances are that you care about keeping your API secure. It’s an important topic to discuss: API exploits are on the rise, and you don’t want unauthorized users accessing your data. A big part of that security is implementing API authentication and API authorization. These API access control measures are a foundational aspect of API security.