Using Service Mesh Within Your Kubernetes Environment
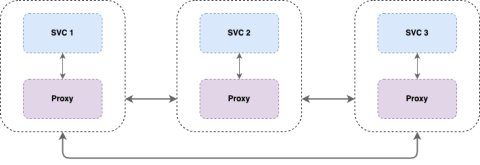
Container technologies are always evolving — and we're not talking Tupperware here. Over the past years, service mesh has emerged as a crucial component for managing complex, distributed systems. As organizations increasingly adopt Kubernetes for orchestrating their containerized applications, understanding how to effectively implement and utilize a service mesh within this environment becomes paramount.