Systems | Development | Analytics | API | Testing
BI
What is next for Yellowfin?
Unravel Data Unveils Most Advanced AI-Powered DataOps
New edition enables data professionals to gain end-to-end visibility and more effectively optimize cost and performance of modern data stack
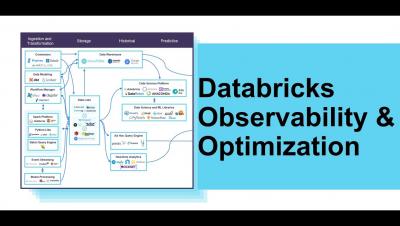
Announcing the Unravel Winter Release
Today, we’re excited to announce the Unravel Winter Release ! This winter release introduces major enhancements and improvements across the platform, including comprehensive cost management for Databricks, support for Delta Lake on Databricks, data observability for Google BigQuery, interactive pre-check before installation and upgrade.
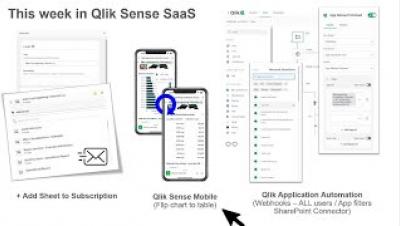
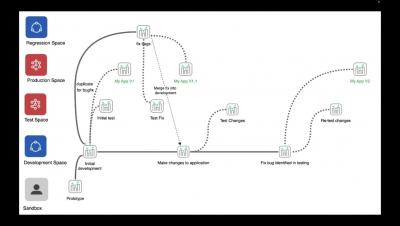
Systems development lifecycle (SDLC) with the Qlik Active Intelligence Platform -Part 1
Start delivering trusted insights - here's how
Data may be everywhere, but it isn’t free. It takes a lot of work and infrastructure to turn raw data into useful insights. Research suggests that the cost of handling data is only going to increase, by as much as 50% over five years. The same source suggests that part of that cost comes from confusion — users may spend up to 40% of their time searching for data and up to 30% of their time on data cleansing. The issue here is data trust.
Playing Offense Against Ransomware with a Modern Data Infrastructure
Has your company faced a ransomware attack yet? If not, count yourself lucky, for now. A June 2021 article in Cybersecurity Ventures predicts that ransomware will cost its victims approximately $265 billion annually by 2031. And, according to CRN, “Victims of the 10 biggest cyber and ransomware attacks of 2021 were hit with ransom demands totaling nearly $320 million.”