Systems | Development | Analytics | API | Testing
%term
How to Handle the Incompatible Types Error in Java
Variables are memory containers used to store information. In Java, every variable has a data type and stores a value of that type. Data types, or types for short, are divided into two categories: primitive and non-primitive. There are eight primitive types in Java: byte, short, int, long, float, double, boolean and char. These built-in types describe variables that store single values of a predefined format and size.
9 Expert Tips for Using Snowflake
G2 Winter 2022 Fastest Implementation: DreamFactory Awarded!
Migrating Data During a Merger or Acquisition
Since I’m now migrating NodeGraph’s processes to Qlik, I thought it may be a good time to talk about migrating data during a merger or acquisition. There are many aspects to consider. Here are some of my thoughts on why companies merge or migrate data landscapes, common M&A migration pitfalls and how to avoid them, the time and cost involved migrating data during a merger or acquisition, and other topics.
Apigee 2021: A year of innovations
Apigee is committed to continually innovating new capabilities and solutions for our customers, and 2021 saw new product launches, partnerships, and best practices for managing your expanding range of business-critical use cases. Here are some of our favorite stories from 2021.
logit.io
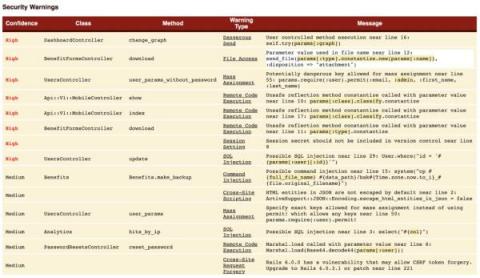
Security Risks On Rails: Misconfiguration and Unsafe Integrations
In the third and final article of our series on the OWASP Top 10 Web Application Security Risks, we’ll explore the lesser-known risks associated with the development of web applications on Rails when it comes to threats involving security misconfiguration, JSON escaping, etc.
How to Price Your SaaS Product: 9 Tips to Get Started
Embracing Failure With Gremlin Chaos Engineering
In this episode of Kongcast, I spoke with Jason Yee, director of advocacy at Gremlin, about the concept of chaos engineering, why even the best engineers can’t control everything, and tools and tactics to help build app resiliency. Check out the transcript and video from our conversation below, and be sure to subscribe to get email alerts for the latest new episodes.