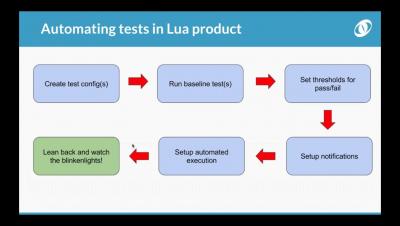
Successful Methodologies with Talend
For those who are familiar with my previous Talend blogs perhaps you’ve noticed that I like to talk about building better solutions through design patterns and best practices. My blogs also tend to be a bit long. Yet you read them; many thanks for that! This blog is going to focus on methodologies as they apply to Talend solutions.