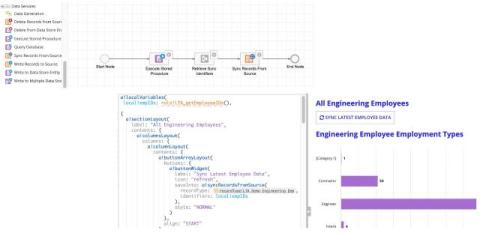
Enhancing security and compliance for Large Enterprises
Discover how Bitrise is transforming to meet the demands of large enterprises. Learn about our past updates, current enhancements, and future plans to ensure robust security, compliance, and centralized management.