Systems | Development | Analytics | API | Testing
Latest Posts
Exploring Event-Driven Architecture: A Beginner's Guide for Cloud Native Developers
Classical request/response architecture is driven by procedure calls, where a caller waits for the call to finish, and the call continues until the work is done. Each incoming call is broken into smaller procedure calls, which may in turn call other procedures. In contrast, event-driven architecture (EDA) is driven by events such as user actions, sensor outputs, or messages from other programs/threads, which determines the execution flow.
23 Useful .Net Libraries for Your Next Project
Not every development framework is capable of creating a modern application. One of the reasons why.NET is considered one of the best frameworks is because it offers a variety of libraries that can help developers create these modern apps. Its features are also updated using low code and the deployment of high-scalable and accomplished apps.
How to Fix Python's "List Index Out of Range" Error in For Loops
The List Index Out of Range error often occurs when working with lists and for loops. You see, in Python, when you attempt to access an element using an index that lies outside the valid index range of the list, you're essentially telling the program to fetch something that isn't there, resulting in this common error. It's the interpreter's way of signaling that there's a misalignment in your expectations of the list's size and the actual indices present.
What's New in Kong Ingress Controller 2.11?
Will ChatGPT Save the Chatbot Industry? (Part II)
In part one of this two part series, I reviewed the history of the chatbot, my 2003 patent, and the reasons why the conditions weren’t right for the type of chat experience we’re all now enjoying with ChatGPT. For part two, we get into what has changed and the different ways enterprises can drive modern chatbot experiences with ChatGPT.
A step-by-step guide to building a Ruby gem from scratch
From Core to Coreless: A Paradigm Shift in Banking
In the ever-evolving world of banking technology, the traditional core banking systems have long been the backbone of financial institutions. However, the limitations and challenges associated with these systems have paved the way for a paradigm shift towards coreless banking. Let us delve into the concept of coreless banking and explore how it is reshaping the banking industry.
Mastering Test Automation with Command Line Interface + A Free CLI Cheatsheet!
At Ghost Inspector, we are passionate about empowering our users with testing solutions that ensure everything on your website or app works and looks the way it should. Our Command Line Interface (CLI) is one of those solutions, allowing you to simplify the process of scripting interactions with the Ghost Inspector API.
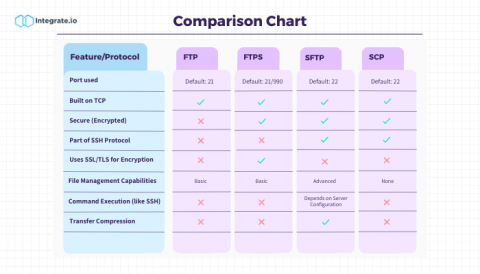
The Complete Guide to FTP, FTPS, SFTP, and SCP
In the digital age, data transfer is integral to operations for businesses of all sizes. While Extract, Transform, and Load (ETL) processes have become fundamental for moving raw data to destinations like data warehouses, the protocols you use to transfer these files can impact the efficiency and security of the entire operation. Dive into our comprehensive guide, as we shed light on the most popular file transfer protocols and their relevance in today's tech landscape.