Systems | Development | Analytics | API | Testing
Analytics
The Clear SHOW - S02E02 - .get_local_copy()
Enriching your Kafka Data Platform with Metadata
How to Learn SEO: Free Resources to Start with
Bigtable vs. BigQuery: What's the difference?
Many people wonder if they should use BigQuery or Bigtable. While these two services have a number of similarities, including "Big" in their names, they support very different use cases in your big data ecosystem. At a high level, Bigtable is a NoSQL wide-column database. It's optimized for low latency, large numbers of reads and writes, and maintaining performance at scale.
Xplenty PII & PHI transformations
Personally identifiable information (PII) and protected health information (PHI) are two types of sensitive data that fall under one or more data privacy regulations. HIPAA and GDPR are examples of the regulations that govern what organizations can and need to do with PII and PHI. When you work with large data sets, it can be challenging to maintain compliance with these regulations.
Deep Learning with Nvidia GPUs in Cloudera Machine Learning
In our previous blog post in this series, we explored the benefits of using GPUs for data science workflows, and demonstrated how to set up sessions in Cloudera Machine Learning (CML) to access NVIDIA GPUs for accelerating Machine Learning Projects.
The rise of analytics-first software
We've moved from desktop to SaaS, to a real UX focus. Now we're seeing new vendors that are analytics-first. They’re creating new applications that are challenging the established players. Historically, applications were transaction-first; you build your software thinking about your workflow or the transactions that you want people to do.
APAC ThoughtSpot User Group - April 15, 2021
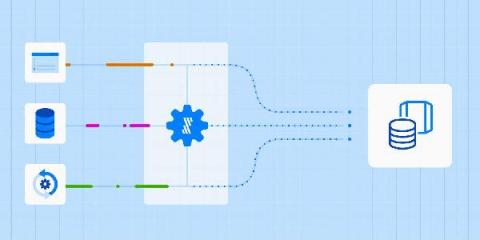
Why Your Data Integration Solution Needs Automated Data Connectors
Custom code to connect with data APIs is quickly becoming a thing of the past.