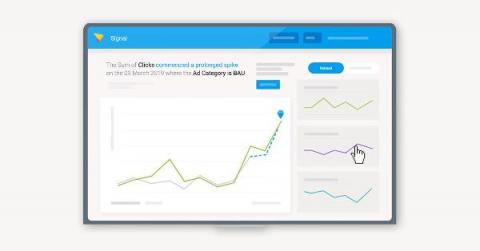
5 key business benefits of Automated Business Monitoring
Understandably, however, the many automation, AI and machine learning technologies that come with modern analytics solutions can sometimes be hard to keep up with. One area we get asked a lot about is ABM, which we offer with Yellowfin Signals, and what exact advantages it brings to the table for everyday analysis and insight generation.