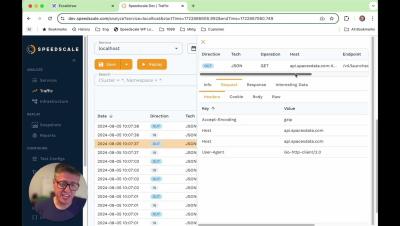
How to get started with a local kubernetes development environment
Mocks can be useful, but hard to build. You can use them as backends for development, or even tests (like load and performance testing). Speedscale takes the legwork out of building mocks, by modeling them after real observed traffic. This video covers a real-world example of how to use mocks to backend a JMeter load test.