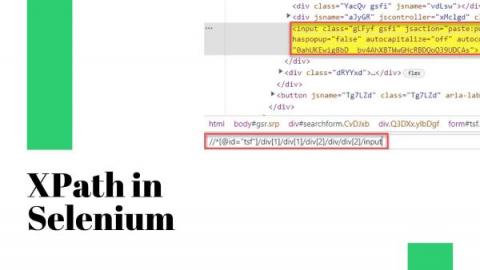
UX & Testing: UX Lessons Learned From My Real-Life Experiences - Part 1
The key differentiator that distinguishes good software from outstanding software is the user experience. Software testers should go beyond just checking the functionality of the product. Software Testing is one of those fields where the more you know the better it is. Testers need to be generalists to be effective at work, someone with broad knowledge across many topics and expertise in a few.