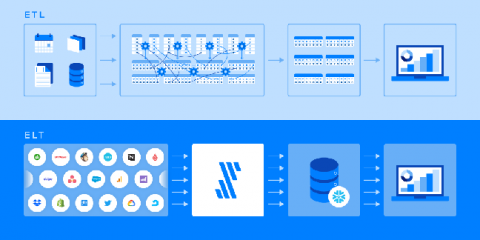
Automating Healthcare Data to Improve Patient Outcomes
Healthcare organizations like yours are riddled with mountains of data and document streams coming in each day. Whether it’s patient records, claims, denials, remits, or clinician credentials… the list goes on. All these items can quickly create chaos and confusion without proper organization protocols in place to handle this data deluge. When employees are tasked with manually handling inbound document management, there is the potential for a wide array of complications, including.